 In last few years, we are all being shocked by the revelations of the most widespread surveillance program by the “Five Eye” namely U.S., U.K., Canada, Australia and New Zealand. Not to mention almost everyday hackers try to bring down networks and steal secret credentials causing huge financial losses to businesses. While most of us are aware of such spying activities and more, it becomes important to know your privacy and what are the ways in which you can still keep them. This is where knowing about it and the tools can really help.
In last few years, we are all being shocked by the revelations of the most widespread surveillance program by the “Five Eye” namely U.S., U.K., Canada, Australia and New Zealand. Not to mention almost everyday hackers try to bring down networks and steal secret credentials causing huge financial losses to businesses. While most of us are aware of such spying activities and more, it becomes important to know your privacy and what are the ways in which you can still keep them. This is where knowing about it and the tools can really help.
The Various Attacks you may face
The basic ways of attacks can be broken down to – syntactic and semantic. Syntactic are straight-forward techniques that try to crack open a system from a small vulnerability which employ software solutions like Trojans, worms and viruses – an example being the Stuxnet virus that crippled Iran’s nuclear plans. Semantic attacks are more about information dispersal and are a more social approach than technical – disseminating wrong information for certain gains. Then there are attacks to deny you access to your own servers – “denial of service” attacks.
How it’s done
Let us understand how exactly it is done – the basic idea is port scanning for vulnerabilities, which uses 3-way handshaking mechanism of TCP. Thus securing your port message exchanges with SYN packets from random destinations becomes an essential part of employing any security tool. While many may go the route of traditional ways i.e. Firewalls and TLS with digital certificates, the amount of computing power available to spying agencies can crack even 768-bit RSA cryptosystems within certain time-frame demonstrating their enormous power.
TCP Stealth – The Way Out
Where there is a will, there is a way and when there are a million angry fuming network admins, there is a software solution! TCP Stealth is an open-source software, right now compatible with GNU/Linux OS, and uses a variation of port knocking to allow handshakes with authorized clients only and denying any other unidentified port SYN packets. This is especially useful for systems with small user groups where a passphrase can be easily shared. It designed with GHCQ-grade offensive techniques in mind and also accounts for compromised infrastructure.
Some Other Tools
While TCP Stealth is a nice addition, sometimes you may have to look at other tools too. Most attacks often happen are web and email based and thus those channels need to be secured. Further,cloud security as many are providing services via SaaS technique. Use penetration testing on your system before deployment and make sure all holes are plugged – there are many tools like MetaSploit, WireShark, etc. Continuously releasing patches for identified vulnerabilities can also keep things in control as many corporations do.
With increasing cyber terrorism and spying on the horizon, it is probably time you ramp your security and continuously strive to improve it. Many make the mistake of not being proactive and thus being exposed by hackers who themselves are quick and rely on 0-day attacks. Traditional tools can only get you so far, so be aware of new attacks, test for vulnerabilities and make it a compulsory prerogative with significant budget, not just an afterthought.

 Why Your Link Building Efforts Might Fail
Why Your Link Building Efforts Might Fail  How to Request or Give Remote Control in a FaceTime Call on iPhone
How to Request or Give Remote Control in a FaceTime Call on iPhone  The Rise of Intelligent Automation in Business Operations
The Rise of Intelligent Automation in Business Operations  The Best Ideas for Designing Your Custom Printed Ring Binder
The Best Ideas for Designing Your Custom Printed Ring Binder  How Technology is Changing the Way We Play Hearts
How Technology is Changing the Way We Play Hearts  The Rise of Open Source: A Journey to Innovation and Collaboration
The Rise of Open Source: A Journey to Innovation and Collaboration 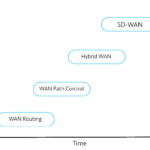 How SD-WAN Is Revolutionizing Business Networks
How SD-WAN Is Revolutionizing Business Networks  Effective Digital Advertising Strategies for Modern Businesses
Effective Digital Advertising Strategies for Modern Businesses  Tips for Marketing Dental Packages: Easy Ways to Grow Your Reach
Tips for Marketing Dental Packages: Easy Ways to Grow Your Reach 