Replaced Smashed Screens of Smartphone –Threat of Devices Hacked
According to a study, smartphones users who have replaced their smashed screens at third party outlets may face threat of having their devices hacked. Researchers at the University of the Negev have informed that replacing screens of Android smartphones could be deployed in stealing personal details and take control of a repaired device.
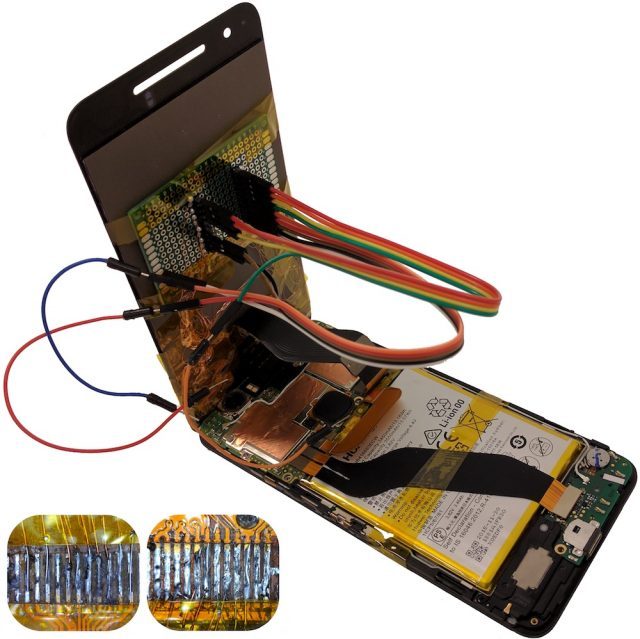
The outbreak is not detectable and could be utilised to relentlessly compromise the smartphone of the victims according to the researchers. Smartphones tends to function through a malicious chip which is said to be inserted within the replacement display and the chip can be applied to the screen with comparative ease. It can then be utilised to hack into the smartphones.
The attack had been demonstrated by the researchers by hijacking a Huawei Nexus 6P smartphones and an LG G Pad 7 tablet. They were capable of recording what had been typed on the affected devices like the passwords, download apps on it and also send the users to malevolent websites. Moreover the researchers could also order the compromised device to take an image of the user and forward it to hackers in an email. With some additional efforts they were also capable of utilising the manipulated screen in assessing the operating system of the affected devices.
Operate on iPhone
The researchers have also informed that the hack could operate on an iPhone too though had not demonstrated the same. The malicious attack is said to be undetectable even to the technicians of smartphones since the malicious chip is made to appear like an official one.
Since it is a physical attack, it goes unnoticed also with anti-virus tools. The researchers have advised the smartphones manufacturers in creating a physical defence system which would be capable of preventing these types of hack on replaced screen devices.
The University of the Negev researchers had mentioned that `a well-motivated adversary could be completely capable of mounting such attacks in a large scale or against specific targets. System designers need to consider replacement components to be beyond the trust boundary of the smartphones and design their defences accordingly. Apple for long has been disapproved of making it complex for third party technicians in replacing the screens of iPhone and iPad.
Consumer watchdog of Australia had sued Apple earlier this year over rights it firmly stopped devices working after the smashed screens of the smartphones had been replaced by third parties.
Researchers had explained that smartphones touchscreens together with the other related hardware components like orientation sensors, wireless charging controllers and NFC readers tend to be produced by third-party manufacturers and not by the phone vendors.
In a paper by the researchers at the Ben-Gurion University of the Negev, it is said that they had raised concern regarding going to third-party fix shops could lead to the possibility of one’s device being hijacked from a relatively simply process of replacing a smashed screen.
The code that is located on the chip can be utilised in installing malicious apps, replace user-selected URLs with phishing URLs, the logging of unlock pattern as well as keyboard inputs together with taking images of the user and forwarding the same through email. Then a hot air blower is utilised in separating the touchscreen controller of the smartphones from the main assembly boards for accessing its copper pads.

 Why Your Link Building Efforts Might Fail
Why Your Link Building Efforts Might Fail  How to Request or Give Remote Control in a FaceTime Call on iPhone
How to Request or Give Remote Control in a FaceTime Call on iPhone  The Rise of Intelligent Automation in Business Operations
The Rise of Intelligent Automation in Business Operations  The Best Ideas for Designing Your Custom Printed Ring Binder
The Best Ideas for Designing Your Custom Printed Ring Binder  How Technology is Changing the Way We Play Hearts
How Technology is Changing the Way We Play Hearts  The Rise of Open Source: A Journey to Innovation and Collaboration
The Rise of Open Source: A Journey to Innovation and Collaboration  How SD-WAN Is Revolutionizing Business Networks
How SD-WAN Is Revolutionizing Business Networks  Effective Digital Advertising Strategies for Modern Businesses
Effective Digital Advertising Strategies for Modern Businesses  Tips for Marketing Dental Packages: Easy Ways to Grow Your Reach
Tips for Marketing Dental Packages: Easy Ways to Grow Your Reach