Two years ago, Sony Pictures came under attack from a group of lethal cyber attackers after releasing a movie which took a humorous view on the North Korean Premier. These attackers called themselves ‘Guardians of Peace’ and went on to create havoc on the Sony website and released a wide amount of internal emails in the public domain. After the Sony Pictures hack the Guardians of Peace went quiet but a recent findings unearthed by a security firm brings some surprising facts about these attackers latest works.
Researchers have stated that they had successfully linked the attacks made by the Guardians of Peace over the years. US government has earlier stated these attackers had coordinated their attacks from North Korea but recent research has revealed they had been active since 2009 and had carried out successful attacks across the globes by attacking computer system mainly in Asia and South Korea.
Security reveals the real culprits behind Sony Pictures hack
A report by the security firm called Novetta has stated that the group of attackers should be termed as ‘Lazarus Group’. It is essentially a biblical reference as this group keeps coming back from the death with a new name and continues its menacing tasks of attacking computer system across the globe.
Novetta has stated that Lazarus Group has used the technique of using unusual attacking group name like ‘WhoIsTeam’, ‘IsOne’, ‘Guardians of Peace’ and others each time it performs a hacking operation. Once the attack has been performed that group simply disappears and nothing is heard from them ever again.
A concentrated effort helps in figuring out the menacing ‘Lazarus Group’
Novetta has worked with the researchers at AlienVault and Kaspersky Lab in order to analyze the pieces of evidences relating to the cyber attacks performed globally. All of these evidences are signaled towards the presence of the Lazarus Group. This group has successfully launched a brutal cyber attack campaign against the South Korean television stations and financial institutions in 2013.
Reaserchers has analyzed the malware, which were used in these attacks, and they found some clues which linked all these attacks to more than forty families of malware presumably developed by the Lazarus Group.
Security researchers tread an explosive path
It is not at all easier for the security researchers to point fingers or make definite attributions due to various reasons. Tom Cross a chief technology officer at an established cyber security firm has stated that it is extremely hard for the security researchers to prove things beyond doubt as they lack great resources, which are at the disposal of the governmental agencies.
Whenever a government makes claim about the origin of the cyber attacks it is basically based on the classified information which can be backed upon. Novetta is currently starting an effort called Operation Blockbuster in order to spread information regarding this group to offer know how in fending off the further attacks in future.

 Why Your Link Building Efforts Might Fail
Why Your Link Building Efforts Might Fail  How to Request or Give Remote Control in a FaceTime Call on iPhone
How to Request or Give Remote Control in a FaceTime Call on iPhone  The Rise of Intelligent Automation in Business Operations
The Rise of Intelligent Automation in Business Operations  The Best Ideas for Designing Your Custom Printed Ring Binder
The Best Ideas for Designing Your Custom Printed Ring Binder  How Technology is Changing the Way We Play Hearts
How Technology is Changing the Way We Play Hearts  The Rise of Open Source: A Journey to Innovation and Collaboration
The Rise of Open Source: A Journey to Innovation and Collaboration 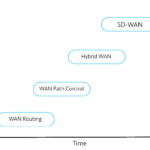 How SD-WAN Is Revolutionizing Business Networks
How SD-WAN Is Revolutionizing Business Networks  Effective Digital Advertising Strategies for Modern Businesses
Effective Digital Advertising Strategies for Modern Businesses  Tips for Marketing Dental Packages: Easy Ways to Grow Your Reach
Tips for Marketing Dental Packages: Easy Ways to Grow Your Reach 
